Hacking a WEP key with airodump on Ubuntu
WEP key can easily be cracked with a simple combination of tools on
Linux machine. The WEP cracking is made easier by the flaws in the
design of the WEP encryption that makes it so vulnerable.
These tools are already inbuilt in the Backtrack linux about which I posted recently. But you can install these hacking tools separately as well on any linux distro.
These steps are made for an Ubuntu machine and uses Debian version which is the format for Ubuntu. Specific version for each each hack tool are available for almost all leading linux versions.
The hack starts-
Install aircrack-ng – on Debian Etch by:
sudo apt-get install aircrack-ng
Then start aircrack-ng to look for wireless networks:
sudo airodump-ng eth1
Then notice the channel number of the wireless network you want to crack.
Quit aircrack-ng and start it again with med specific channel number to collect packages faster:
sudo airodump-ng -c 4 -w dump eth1
Then wait and let it collect about 500K IVS and the try the do the actual crack:
sudo aircrack-ng -b 0a:0b:0c:0d:0e:0f dump-01.cap
The MAC after the -b option is the BSSID of the target and dump-01.cap the file containing the captured packets.
A new project called Pyrit is currently under it’s way. “Pyrit takes a step ahead in attacking WPA-PSK and WPA2-PSK, the protocol that today de-facto protects public WIFI-airspace. The project’s goal is to estimate the real-world security provided by these protocols. Pyrit does not provide binary files or wordlists and does not encourage anyone to participate or engage in any harmful activity. This is a research project, not a cracking tool.
Pyrit’s implementation allows to create massive databases, pre-computing part of the WPA/WPA2-PSK authentication phase in a space-time-tradeoff. The performance gain for real-world-attacks is in the range of three orders of magnitude which urges for re-consideration of the protocol’s security. Exploiting the computational power of GPUs, this is currently by far the most powerful attack against one of the world’s most used security-protocols.”
==================================================================================
Network Hacking Using Command Prompt
-: Network Hacking :-
Network Hacking is generally means gathering information about domain by using tools like Telnet, NslookUp, Ping, Tracert, Netstat, etc.
It also includes OS Fingerprinting, Port Scaning and Port Surfing using various tools.
Ping :- Ping is part of ICMP (Internet Control Message Protocol) which is used to troubleshoot TCP/IP networks. So, Ping is basically a command that allows you to check whether the host is alive or not.
To ping a particular host the syntax is (at command prompt)--
c:/>ping hostname.com
example:- c:/>ping www.google.com

Various attributes used with 'Ping' command and their usage can be viewed by just typing c:/>ping at the command prompt.
Netstat :- It displays protocol statistics and current TCP/IP network connections. i.e. local address, remote address, port number, etc.
It's syntax is (at command prompt)--
c:/>netstat -n

Telnet :- Telnet is a program which runs on TCP/IP. Using it we can connect to the remote computer on particular port. When connected it grabs the daemon running on that port.
The basic syntax of Telnet is (at command prompt)--
c:/>telnet hostname.com
By default telnet connects to port 23 of remote computer.
So, the complete syntax is-
c:/>telnet www.hostname.com port
example:- c:/>telnet www.yahoo.com 21 or c:/>telnet 192.168.0.5 21
Tracert :- It is used to trace out the route taken by the certain information i.e. data packets from source to destination.
It's syntax is (at command prompt)--
c:/>tracert www.hostname.com
example:- c:/>tracert fbtghana.blogspot .com
Here "* * * Request timed out." indicates that firewall installed on that system block the request and hence we can't obtain it's IP address.
various attributes used with tracert command and their usage can be viewed by just typing c:/>tracert at the command prompt.
The information obtained by using tracert command can be further used to find out exact operating system
==================================================================================
Set up your Pen Hacking Lab Network using a Single System
| Contents | |
| Introduction | |
| There are lots of tutorials available on the internet related to hacking but the big problem lies in testing your theoretical skills. Unless you don't have practical exposure to hacking, you cannot really understand the strength of it. The technique I will discuss here will be advantageous for those who have only single system and want to set up a testing network using it. In case you have multiple systems then you can easily test for your skills by making one system as target and other as attacker. | |
 |
|
| But what to do when we have only a single system at our disposal. Need not to worry. Virtual machine is the ultimate solution. You can set up your own hacking network and apply your skills to gain practical exposure to hacking. | |
| Installation & Configuration | |
| The only thing to look for is your systems hardware configuration.
You should have minimum 2 GB RAM but it is highly recommended to use
3 GB RAM for a 32 bit operating system. We will be using Oracle VirtualBox in this tutorial. You can download virtualbox from this link [Reference 1]. Once you have installed Vbox, the next step is to download the Extensions pack. You can get it from this link [Reference 2] Once you have followed these initial steps, you are half done. The next step is to setup a target operating system. Suppose you want to set WINDOWS XP SP2 as the target operating system. You will need a bootable Windows XP SP2 iso for that. You can easily download it from Microsoft website or torrent. You can refer to this quick video tutorial on how to setup a virtual machine using VBox and WIN XP. |
|
| Installing Applications on Virtual Machine | |
| So now you have a virtual machine where
you can test all your applications and hacks. Let us install a
WAMP server and run DVWA over it. For those who are not aware
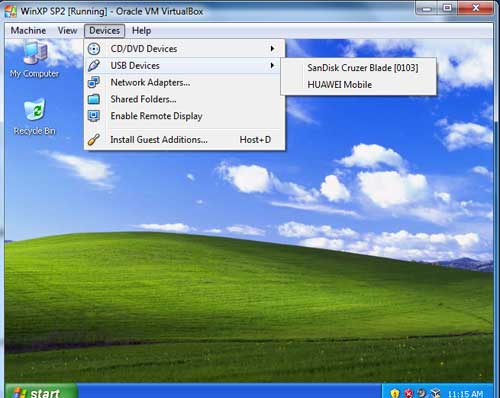
of DVWA can check this link [Reference 3] How to install applications on a virtual machine? Well the process is simple. When your Windows XP Virtual machine is running, then click on the DEVICE tab, move to USB and select your pendrive from the list. |
|
 |
|
| Now you can install anything from a USB drive inside your virtual machine. There is also a facility to create shared folder with your host operating system but I would prefer that you use USB. Shared folder has some issues when your host operating system is Windows 7. You can install different servers, applications, RAT clients etc and play with it. | |
| Advantages of Virtual Machine | |
| Here are some of the major advantages of using virtual machine. | |
|
|
| Take Backup & Save Trouble in Future | |
| There are also some key factors that you should remember which will help you during your pentesting: | |
|
|
 |
|
| Disable the Windows Firewall | |
| The next important thing you can do is disable the windows
firewall and then perform your pentesting as the firewall may
block some of the suspicious activities. Using the default Windows
firewall of XP virtual machine you can also test whether your activity
is traceable or not. This will give you a clear understanding why RATs
are not considered as a suitable hack these days because they are easily
detectable. You can disable the firewall by going to control panel,
clicking on Firewall and then disable it. In this way you can set up a suitable environment for your home experiments. |
|
| Testing your Pen-Testing/Hack Network | |
| Well a good question to ask if you have understood the above
concepts. So far we discussed how to test different tools and techniques
on a virtual operating system. The next step will be how to hack one
virtual machine using the other. The scenario will be similar to
hacking any system on internet so this technique will give you
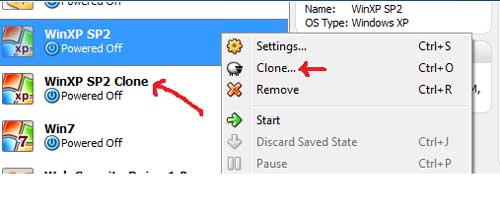
a real time exposure. Interesting... Lets proceed then. This time we will set up another virtual machine using BackTrack [Reference 4] operating system which is one of the most widely used penetration testing operating system by security professionals. The reason which makes Backtrack so popular is: |
|
|
|
| You can download the Backtrack 5 iso from its official website. Its a must have operating system for all. You can follow this simple video to install BT on virtualbox. | |
 | |
| Once you are done with the installation part, the next step is to
make the two virtual machines (BT and WinXP) connect with each other.
There is a simple setting that you will have to make in both the virtual
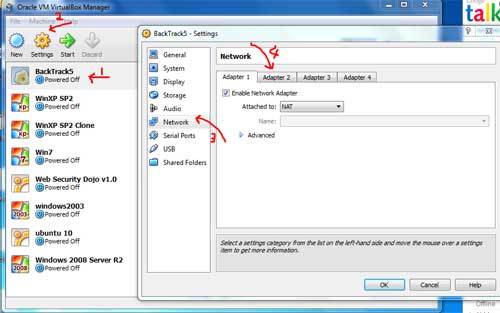
machines. Let's check it out. Select the Backtrack virtual machine, then click on settings tab, then move to "network" settings. You will find that "Adapter 1" is set to NAT adapter. Switch to the "Adapter 2" tab. |
|
 |
|
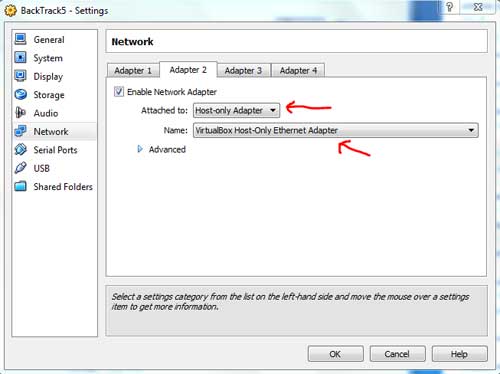
| In the Adapter2 tab, set the adapter as "Host-Only Adapter". Set the name of adapter as "VirtualBox Host Only Ethernet Adapter" . See the figure. | |
 |
|
| Make similar setting changes in your windows XP virtual machine as
well. Now your two virtual machines are ready to connect with each
other. You can check the IP address of Windows machine by using the
ipconfig command in the command prompt and similarly you can check the
IP address of the BT machine using the ifconfig command. Also you can
ping the two machines to check if both are detecting each other (don't
forget to disable the windows firewall else it will filter the ping data
packets). The following image shows my two virtual machines. One is WinXP and other is BT5 with there corresponding ip addresses. Both are running ovr my host operating system Win7. So in all there are 3 operating systems running simultaneously. |
|
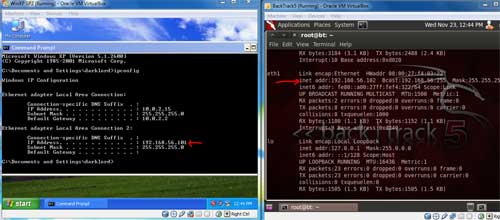 |
|
| Now you can use various options available in Backtrack OS to perform tests on the WinXP box. Let us quickly perform an nmap scan to check the open ports on WinXP machine. | |
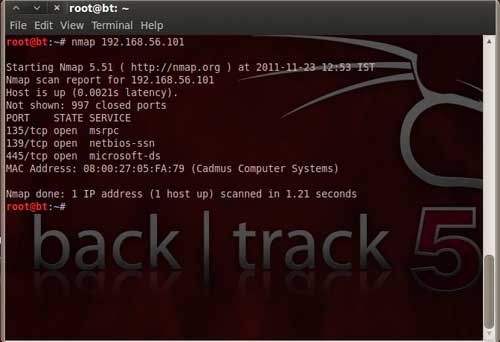 |
|
| As you can see that the target is up and has some open ports as
well. Similarly you can perform several attacks and use the tools
available in Backtrack to penetrate the target windows XP machine
without harming your own operating system. You can use this technique to perform several tests like, |
|
|
|
| References | |
| Conclusion | |
| This is just a quick example for you all to get started with using VM's
for pentesting and hacking. You can further take this tutorial to next
level by experimenting with various flavors of operating systems and try
your hands on them. This can be like a practice battlefield for you before you dive deep into the real fight. ================================================================================== Hacking tools that every hacker must haveWe present another list of the must hacking tools every hacker must have. These toolsmake the life of a hacker much easier and every n00b must first learn how to use these tools first.AIRCRACK Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the all-new PTW attack, thus making the attack much faster compared to other WEP cracking tools. In fact, Aircrack-ng is a set of tools for auditing wireless networks. Site URL: http://www.aircrack-ng.org/ BackTrack BackTrack is a A Linux Distribution focused on penetration testing. Site URL: http://www.bactrack-linux.org BarsWF BarsWF is the worlds fastest md5 bruteforcing password cracker, just in case you didn't already know. It combines using your computers processor with you graphics cards GPU for computing the largest amount of hashes as quickly as possible. It is not unheard of to get 100's of millions of hashes per second when using this application. Prerequisites which really dont need to be mentioned are a processor with SSE2 instruction set, and any nvidia geforce 8 and up graphics card with CUDA support if you want the really fast one, otherwise most decently new nvidia graphics cards bought in the past 2 years should be able to work with this. Site URL: http://3.14.by/en/md5 BLOODSHED IDE Bloodshed IDE is an Integrated Development Environment (IDE) for the C/C++ programming language. Site URL: http://www.bloodshed.net/devcpp.html CAIN AND ABEL Cain and Abel is a Windows password cracker, capable of cracking a variety of hashes, as well as arp poisoning, sniffing the network, etc.. to obtain those password hashes in the first place. Site URL: http://www.oxid.it/cain.html CANVAS Immunity's CANVAS makes available hundreds of exploits, an automated exploitation system, and a comprehensive, reliable exploit development framework to penetration testers and security professionals worldwide. To see CANVAS in action please see the movies at immunitysec.com Supported Platforms and Installations # Windows (requires Python & PyGTK) # Linux # MacOSX (requires PyGTK) # All other Python environments such as mobile phones and commercial Unixes (command line version only supported, GUI may also be available) Exploits # currently over 400 exploits, an average of 4 exploits added every monthly release # Immunity carefully selects vulnerabilities for inclusion as CANVAS exploits. Top priorities are high-value vulnerabilities such as remote, pre-authentication, and new vulnerabilities in mainstream software. # Exploits span all common platforms and applications Payload Options # to provide maximum reliability, exploits always attempt to reuse socket # if socket reuse is not suitable, connect-back is used # subsequent MOSDEF session allows arbitrary code execution, and provides a listener shell for common actions (file management, screenshots, etc) # bouncing and split-bouncing automatically available via MOSDEF # adjustable covertness level Ability to make Custom Exploits # unique MOSDEF development environment allows rapid exploit development Development # CANVAS is a platform that is designed to allow easy development of other security products. Examples include Gleg, Ltd's VulnDisco and the Argeniss Ultimate 0day Exploits Pack. Site URL: http://www.immunitysec.com/products-canvas.shtml CYGWIN Cygwin is the next best thing to using Linux. I personally do not use a windows box period, work, school, or other, unless I have Cygwin installed. It's a large download, but once you get use to using it there's no turning back. I have actually created a condensed copy that I carry around on my flash drive. It comes complete with most Unix/Linux commands, to include the ability to compile things on the fly with gcc, perl, etc.. It has many useful things about it, but the only way to really see the extent of them is to use it yourself unless you like reading pages of technical data to help put you to sleep at night. FYI...Last I checked it was currently managed by RedHat. Site URL: http://www.cygwin.com/ DBAN DBAN- Short for Darik's Boot and Nuke, is a good utility for securely erasing contents of hard disk. It uses encryption and re-writing over drives multiple times for a fairly secure deletion which makes if very difficult if not impossible to recover using forensics. Site URL: http://www.dban.org/about FARONICS DEEP FREEZE Faronics Deep Freeze helps eliminate workstation damage and downtime by making computer configurations indestructible. Once Deep Freeze is installed on a workstation, any changes made to the computer—regardless of whether they are accidental or malicious—are never permanent. Deep Freeze provides immediate immunity from many of the problems that "He-Who-Must-Not-Be-Named." computers today—inevitable configuration drift, accidental system misconfiguration, malicious software activity, and incidental system degradation. Deep Freeze ensures computers are absolutely bulletproof, even when users have full access to system software and settings. Users get to enjoy a pristine and unrestricted computing experience, while IT personnel are freed from tedious helpdesk requests, constant system maintenance, and continuous configuration drift. Site URL: http://www.faronics.com/html/deepfreeze.asp NEMESIS Nemesis is a packet injector utility that is command line based and supports linux and windows. Site URL: http://www.packetfactory.net/projects/nemesis/ GEEKSQUAD MRI GeekSquad MRI is the the Best Buy geek squad repair disc - Code Name MRI - for internal use only, confidential, and a trade secret. This is version 5.0.1.0 - the latest version. The disc has tools to help fix computers - it has AntiVirus, AntiSpyware, Disk Cleaner, Process List, Winsock Fix, etc, all in an attractive and quite usable interface! Site URL: At piratebay or google it. SCAPY Scapy is a packet manipulator used for crafting packets, sending packets, sniffing them etc. Also runs on Linux and Windows. Site URL: http://www.secdev.org/projects/scapy/ TRUECRYPT TrueCrypt- Free open-source disk encryption software. Site URL: http://www.truecrypt.org SKYPELOGVIEW SkypeLogView reads the log files created by Skype application, and displays the details of incoming/outgoing calls, chat messages, and file transfers made by the specified Skype account. You can select one or more items from the logs list, and then copy them to the clipboard, or export them into text/html/csv/xml file.This utility works on any version of Windows starting from Windows 2000 and up to Windows 2008. You don't have to install Skype in order to use this utility. You only need the original log files created by skype, even if they are on an external drive. Site URL: http://www.nirsoft.net/utils/skype_log_view.html PASSWORD FOX PasswordFox is a small password recovery tool that allows you to view the user names and passwords stored by Mozilla Firefox Web browser. By default, PasswordFox displays the passwords stored in your current profile, but you can easily select to watch the passwords of any other Firefox profile. For each password entry, the following information is displayed: Record Index, Web Site, User Name, Password, User Name Field, Password Field, and the Signons filename. This utility works under Windows 2000, Windows XP, Windows Server 2003, and Windows Vista. Firefox should also be installed on your system in order to use this utility. Site URL: http://www.nirsoft.net/utils/passwordfox.html NESSUS Nessus has been around for a little more than a little while now and has gone from free to almost free to it's gonna cost ya. I'm not really sure regarding the newest updates as I haven't used it since it lost it's freedom, but I will say it has plugins for everything under the sun! It is mainly used for network and server scanning and has the ability to test and create a client/server connection between yourself and the host you're testing with. Site URL: http://www.nessus.org/nessus/ RAINBOW CRACK RainbowCrack is a general propose implementation of Philippe Oechslin's faster time-memory trade-off technique. In short, the RainbowCrack tool is a hash cracker. A traditional brute force cracker try all possible plaintexts one by one in cracking time. It is time consuming to break complex password in this way. The idea of time-memory trade-off is to do all cracking time mabait in advance and store the result in files so called "rainbow table". It does take a long time to precompute the tables. But once the one time mabait is finished, a time-memory trade-off cracker can be hundreds of times faster than a brute force cracker, with the help of precomputed tables. Site URL: http://www.antsight.com/zsl/rainbowcrack/ UNETBOOTIN UNetbootin - An application to install an operating system to a flash drive or to a hard disk by either using the pre-downloaded iso file or by downloading the operating system through the application. Site URL: http://unetbootin.sourceforge.net/ VISUAL STUDIO 2010 Visual Studio 2010- A development environment, and programmers best friend when it comes to designing windows applications. A little pricey, but free for academic use under the MSDNAA. Site URL: http://www.microsoft.com/visualstudio/en-us WINHEX Winhex is a hexadecimal editor, particularly helpful in the realm of computer forensics, data recovery, low-level data processing, and IT security. Also a advanced tool for everyday and emergency use. Code: [Check Download Links] http://www.x-ways.net/winhex/ WPE PRO Winsock Packet Editor (WPE) Pro is a packet sniffing/editing tool which is generally used to hack multiplayer games. WPE Pro allows modification of data at TCP level. Using WPE Pro one can select a running process from the memory and modify the data sent by it before it reaches the destination. It can record packets from specific processes, then analyze the information. You can setup filters to modify the packets or even send them when you want in different intervals. WPE Pro could also be a useful tool for testing thick client applications or web applications which use applets to establish socket connections on non http ports. Site URL: http://wpepro.net/ IDP Interactive Disassembler Pro (IDP) . Supports 80x86 binaries and FLIRT, a unique Fast Library Identification and Recognition Technology that automagically recognizes standard compiler library calls. Widely used in COTS validation and hostile code analysis. In short it's what we like to call the "Reverse Engineer's Wet Dream". Site URL: http://www.hex-rays.com/idapro/ HPING Hping is a command-line TCP/IP assembler that supports TCP, ICMP, UDP and RAW-IP protocols. also works on Unix systems, Windows, Sun and MacOS's. Site URL: http://www.hping.org/ JOHN THE RIPPER John the Ripper- free open-source software (if you want to buy you can always get the pro version) John has been, and continues to still be, the most famous and most widely used password cracker for linux/unix systems. Things everyone likes about it: It's fast, it has support for cracking a lot of different but commonly used hash types, and it's able to run on just about anything. Site URL: http://www.openwall.com/john/ ================================================================================== HACKING TECHNIQUES IN WIRELESS NETWORKS LESSON 1
TABLE OF CONTENTS
1. Introduction.
2. Wireless LAN Overview
2.1 Stations and Access Points
2.2 Channels
2.3 WEP
2.4 Infrastructure and Ad Hoc
Modes
2.5 Frames
2.6 Authentication
2.7 Association
3. Wireless Network Sniffing
3.1 Passive Scanning
3.2 Detection of SSID
3.3 Collecting the MAC
Addresses
3.4 Collecting the Frames for
Cracking WEP
3.5 Detection of the Sniffers
4. Wireless Spoofing
4.1 MAC Address Spoofing
4.2 IP spoofing
4.3 Frame Spoofing
5. Wireless Network Probing
5.1 Detection of SSID
5.2 Detection of APs and
stations
5.3 Detection of Probing
6. AP Weaknesses
6.1 Configuration
6.2 Defeating MAC Filtering
6.3 Rogue AP
6.4 Trojan AP
6.5 Equipment Flaws
7. Denial of Service
7.1 Jamming the Air Waves
7.2 Flooding with Associations
7.3 Forged Dissociation
7.4 Forged Deauthentication
7.5 Power Saving
8. Man-in-the-Middle Attacks
8.1 Wireless MITM
8.2 ARP Poisoning
8.3 Session Hijacking
9. War Driving
9.1 War chalking
9.2 Typical Equipment
10. Wireless Security Best Practices
10.1 Location of the APs
10.2 Proper Configuration
10.3 Secure Protocols
10.4 Wireless IDS
10.5 Wireless Auditing
10.6 Newer Standards and
Protocols
10.7 Software Tools
11.Conclusion
GLOSSARY
Cross References
ABSTRACTS
This
article describes IEEE 802.11-specific hacking techniques that attackers have
used, and suggests various defensive measures. We describe sniffing, spoofing
and probing in the context of wireless networks. We describe how SSIDs
can be determined, how a sufficiently large number of frames can be collected
so that WEP can be cracked. We show how easy it is to cause
denial-of-service through jamming and through forged disassociations and
deauthentications. We also explain three man-in-the-middle attacks using
wireless networks. We give a list of selected open-source tools. We
summarize the activity known as war driving. We conclude the article with
several recommendations that will help improve security at a wireless
deployment site.
1. Introduction
Wireless
networks broadcast their packets using radio frequency or optical
wavelengths. A modern laptop computer can listen in. Worse, an
attacker can manufacture new packets on the fly and persuade wireless stations
to accept his packets as legitimate.
We
use the term hacking as described below.
hacker
n. [originally, someone who makes furniture with an axe] 1. A
person who enjoys exploring the details of programmable systems and how to
stretch their capabilities, as opposed to most users, who prefer to learn only
the minimum necessary. 2. One who programs enthusiastically (even
obsessively) or who enjoys programming rather than just theorizing about
programming. 3. A person capable of appreciating hack value. 4. A
person who is good at programming quickly. 5. An expert at a
particular program, or one who frequently does work using it or on it; as in `a
Unix hacker'. (Definitions 1 through 5 are correlated, and people who fit them
congregate.) 6. An expert or enthusiast of any kind. One might be
an astronomy hacker, for example. 7. One who enjoys the
intellectual challenge of creatively overcoming or circumventing limitations. 8. [deprecated]
A malicious meddler who tries to discover sensitive information by poking
around. Hence `password hacker', `network hacker'. The correct term for this
sense is cracker.
From The Jargon
Dictionary http://info.astrian.net/jargon/
This article describes IEEE 802.11-specific hacking
techniques that attackers have used, and suggests various defensive measures.
It is not an overview of security features proposed in WPA or IEEE
802.11i. We do not consider legal implications, or the intent behind such
hacking, whether malevolent or benevolent. The article’s focus is in
describing techniques, methods, analyses and uses in ways unintended by
the designers of IEEE 802.11.
2. Wireless LAN Overview
In
this section, we give a brief overview of wireless LAN (WLAN) while emphasizing
the features that help an attacker. We assume that the reader is familiar
with the TCP/IP suite (see, e.g., [Mateti 2003]).
IEEE
802.11 refers to a family of specifications (www.ieee802.org/11/)
developed by the IEEE for over-the-air interface between a wireless
client and an AP or between two wireless clients. To be called
802.11 devices, they must conform to the Medium Access Control (MAC) and
Physical Layer specifications. The IEEE 802.11 standard covers the Physical
(Layer 1) and Data Link (Layer 2) layers of the OSI Model. In this
article, we are mainly concerned with the MAC layer and not the variations of
the physical layer known as 802.11a/b/g.
2.1 Stations and Access Points
A
wireless network interface card (adapter) is a device, called a station,
providing the network physical layer over a radio link to another station.
An access point (AP) is a station that provides frame
distribution service to stations associated with it. The AP itself
is typically connected by wire to a LAN.
The
station and AP each contain a network interface that has a Media Access
Control (MAC) address, just as wired network cards do. This address is a
world-wide-unique 48-bit number, assigned to it at the time of manufacture. The
48-bit address is often represented as a string of six octets separated by
colons (e.g., 00:02:2D:17:B9:E8) or hyphens
(e.g., 00-02-2D-17-B9-E8). While
the MAC address as assigned by the manufacturer is printed on the device, the
address can be changed in software.
Each
AP has a 0 to 32 byte long Service Set Identifier (SSID) that is also commonly
called a network name. The SSID is used to segment the airwaves for
usage. If two wireless networks are physically close, the SSIDs label the
respective networks, and allow the components of one network to ignore those of
the other. SSIDs can also be mapped to virtual LANs; thus, some APs support
multiple SSIDs. Unlike fully qualified host names (e.g.,
gamma.cs.wright.edu), SSIDs are not registered, and it is possible that two
unrelated networks use the same SSID.
2.2 Channels
The
stations communicate with each other using radio frequencies between 2.4 GHz
and 2.5 GHz. Neighboring channels are only 5 MHz apart. Two wireless
networks using neighboring channels may interfere with each other.
2.3 WEP
Wired
Equivalent Privacy (WEP) is a shared-secret key encryption system used to
encrypt packets transmitted between a station and an AP. The WEP
algorithm is intended to protect wireless communication from eavesdropping. A
secondary function of WEP is to prevent unauthorized access to a wireless
network. WEP encrypts the payload of data packets. Management and
control frames are always transmitted in the clear. WEP uses the RC4
encryption algorithm. The shared-secret key is either 40 or 104 bits
long. The key is chosen by the system administrator.
This key must be shared among all the stations and the AP using mechanisms
that are not specified in the IEEE 802.11.
2.4 Infrastructure and Ad Hoc Modes
A
wireless network operates in one of two modes. In the ad hoc mode,
each station is a peer to the other stations and communicates directly with
other stations within the network. No AP is involved. All
stations can send Beacon and Probe frames. The ad hoc mode stations form an
Independent Basic Service Set (IBSS).
A
station in the infrastructure mode communicates only with an AP. Basic
Service Set (BSS) is a set of stations that are logically associated with each
other and controlled by a single AP. Together they operate as a fully connected
wireless network. The BSSID is a 48-bit number of the same format as a
MAC address. This field uniquely identifies each BSS. The value of this field
is the MAC address of the AP.
2.5 Frames
Both
the station and AP radiate and gather 802.11 frames as needed. The format
of frames is illustrated below. Most of the frames contain IP packets.
The other frames are for the management and control of the wireless connection.
There
are three classes of frames. The management frames
establish and maintain communications. These are of Association request,
Association response, Reassociation request, Reassociation response, Probe
request, Probe response, Beacon, Announcement traffic indication message,
Disassociation, Authentication, Deauthentication types. The SSID is part
of several of the management frames. Management messages are always sent in the
clear, even when link encryption (WEP or WPA) is used, so the SSID is visible
to anyone who can intercept these frames.
The
control frames help in the delivery of data.
The
data frames encapsulate the OSI Network Layer packets. These
contain the source and destination MAC address, the BSSID, and the TCP/IP
datagram. The payload part of the datagram is WEP-encrypted.
2.6 Authentication
Authentication
is the process of proving identity of a station to another station or AP.
In the open system authentication, all stations are authenticated without any
checking. A station A sends an Authentication management frame that
contains the identity of A, to station B. Station B replies with a frame
that indicates recognition, addressed to A. In the closed network
architecture, the stations must know the SSID of the AP in order to
connect to the AP. The shared key authentication uses a standard
challenge and response along with a shared secret key.
2.7 Association
Data
can be exchanged between the station and AP only after a station is associated
with an AP in the infrastructure mode or with another station in the ad hoc
mode. All the APs transmit Beacon frames a few times each second that
contain the SSID, time, capabilities, supported rates, and other
information. Stations can chose to associate with an AP based on the
signal strength etc. of each AP. Stations can have a null SSID that
is considered to match all SSIDs.
The
association is a two-step process. A station that is currently unauthenticated
and unassociated listens for Beacon frames. The station selects a BSS to join.
The station and the AP mutually authenticate themselves by exchanging
Authentication management frames. The client is now authenticated, but
unassociated. In the second step, the station sends an Association
Request frame, to which the AP responds with an Association Response frame that
includes an Association ID to the station. The station is now
authenticated and associated.
A
station can be authenticated with several APs at the same time, but associated
with at most one AP at any time. Association implies
authentication. There is no state where a station is associated but not
authenticated.
3. Wireless Network Sniffing
Sniffing
is eavesdropping on the network. A (packet) sniffer is a program
that intercepts and decodes network traffic broadcast through a medium.
Sniffing is the act by a machine S of making copies of a network packet sent by
machine A intended to be received by machine B. Such sniffing, strictly
speaking, is not a TCP/IP problem, but it is enabled by the choice of broadcast
media, Ethernet and 802.11, as the physical and data link layers.
Sniffing
has long been a reconnaissance technique used in wired networks.
Attackers sniff the frames necessary to enable the exploits described in later
sections. Sniffing is the underlying technique used in tools that monitor
the health of a network. Sniffing can also help find the easy kill as in
scanning for open access points that allow anyone to connect, or capturing the
passwords used in a connection session that does not even use WEP, or in
telnet, rlogin and ftp connections.
It
is easier to sniff wireless networks than wired ones. It is easy to sniff the
wireless traffic of a building by setting shop in a car parked in a lot as far
away as a mile, or while driving around the block. In a wired network, the
attacker must find a way to install a sniffer on one or more of the hosts in
the targeted subnet. Depending on the equipment used in a LAN, a sniffer
needs to be run either on the victim machine whose traffic is of interest or on
some other host in the same subnet as the victim. An attacker at large on
the Internet has other techniques that make it possible to install a sniffer
remotely on the victim machine.
3.1 Passive Scanning
Scanning
is the act of sniffing by tuning to various radio channels of the devices. A passive
network scanner instructs the wireless card to listen to each channel for a few
messages. This does not reveal the presence of the scanner.
An
attacker can passively scan without transmitting at all. Several modes of
a station permit this. There is a mode called RF monitor mode that
allows every frame appearing on a channel to be copied as the radio of the
station tunes to various channels. This is analogous to placing a wired
Ethernet card in promiscuous mode. This mode is not enabled by default.
Some wireless cards on the market today have disabled this feature in the
default firmware. One can buy wireless cards whose firmware and corresponding
driver software together permit reading of all raw 802.11 frames. A
station in monitor mode can capture packets without associating with
an AP or ad-hoc network. The so-called promiscuous mode allows
the capture of all wireless packets of an associated network. In this mode,
packets cannot be read until authentication and association are completed.
An
example sniffer is Kismet (http://www.kismetwireless.net).
An example wireless card that permits RF monitor modes is Cisco Aironet
AIR-PCM342.
3.2 Detection of SSID
The
attacker can discover the SSID of a network usually by passive scanning because
the SSID occurs in the following frame types: Beacon, Probe Requests, Probe
Responses, Association Requests, and Reassociation Requests. Recall that
management frames are always in the clear, even when WEP is enabled.
On
a number of APs, it is possible to configure so that the SSID transmitted in
the Beacon frames is masked, or even turn off Beacons altogether. The
SSID shown in the Beacon frames is set to null in the hope of making the WLAN
invisible unless a client already knows the correct SSID. In such a case,
a station wishing to join a WLAN begins the association process by sending
Probe Requests since it could not detect any APs via Beacons that match its
SSID.
If
the Beacons are not turned off, and the SSID in them is not set to null, an
attacker obtains the SSID included in the Beacon frame by passive scanning.
When
the Beacon displays a null SSID, there are two possibilities. Eventually,
an Associate Request may appear from a legitimate station that already has a
correct SSID. To such a request, there will be an Associate Response
frame from the AP. Both frames will contain the SSID in the clear, and
the attacker sniffs these. If the station wishes to join any available
AP, it sends Probe Requests on all channels, and listens for Probe Responses
that contain the SSIDs of the APs. The station considers all Probe
Responses, just as it would have with the non-empty SSID Beacon frames, to
select an AP. Normal association then begins. The attacker waits to sniff
these Probe Responses and extract the SSIDs.
If Beacon
transmission is disabled, the attacker has two choices. The attacker can
keep sniffing waiting for a voluntary Associate Request to appear from a
legitimate station that already has a correct SSID and sniff the SSID as
described above. The attacker can also chose to actively probe by
injecting frames that he constructs, and then sniffs the response as described
in a later section.
When
the above methods fail, SSID discovery is done by active scanning (see
Section 5).
3.3 Collecting the MAC Addresses
The
attacker gathers legitimate MAC addresses for use later in constructing spoofed
frames. The source and destination MAC addresses are always in the clear in all
the frames. There are two reasons why an attacker would collect MAC
addresses of stations and APs participating in a wireless network. (1)
The attacker wishes to use these values in spoofed frames so that his station
or AP is not identified. (2) The targeted AP may be controlling access by
filtering out frames with MAC addresses that were not registered.
3.4 Collecting the Frames for Cracking WEP
The
goal of an attacker is to discover the WEP shared-secret key. Often, the
shared key can be discovered by guesswork based on a certain amount of social
engineering regarding the administrator who configures the wireless LAN and all
its users. Some client software stores the WEP keys in the operating
system registry or initialization scripts. In the following, we assume
that the attacker was unsuccessful in obtaining the key in this manner.
The attacker then employs systematic procedures in cracking the WEP. For
this purpose, a large number (millions) of frames need to be collected because
of the way WEP works.
The
wireless device generates on the fly an Initialization Vector (IV) of
24-bits. Adding these bits to the shared-secret key of either 40 or 104
bits, we often speak of 64-, or 128-bit encryption. WEP generates a
pseudo-random key stream from the shared secret key and the IV. The CRC-32
checksum of the plain text, known as the Integrity Check (IC) field, is
appended to the data to be sent. It is then exclusive-ORed with the
pseudo-random key stream to produce the cipher text. The IV is
appended in the clear to the cipher text and transmitted. The receiver extracts
the IV, uses the secret key to re-generate the random key stream, and
exclusive-ORs the received cipher text to yield the original plaintext.
Certain
cards are so simplistic that they start their IV as 0 and increment it by 1 for
each frame, resetting in between for some events. Even the better cards
generate weak IVs from which the first few bytes of the shared key can be
computed after statistical analyses. Some implementations generate fewer
mathematically weak vectors than others do.
The
attacker sniffs a large number of frames from a single BSS. These frames
all use the same key. The mathematics behind the systematic computation
of the secret shared key from a collection of cipher text extracted from these
frames is described elsewhere in this volume. What is needed however
is a collection of frames that were encrypted using “mathematically-weak” IVs.
The number of encrypted frames that were mathematically weak is a small
percentage of all frames. In a collection of a million frames, there may
only be a hundred mathematically weak frames. It is conceivable that the
collection may take a few hours to several days depending on how busy the WLAN
is.
Given
a sufficient number of mathematically weak frames, the systematic computation
that exposes the bytes of the secret key is intensive. However, an
attacker can employ powerful computers. On an average PC, this may take a
few seconds to hours. The storage of the large numbers of frames is in
the several hundred-mega bytes to a few giga bytes range.
An
example of a WEP cracking tool is AirSnort ( http://airsnort.shmoo.com ).
3.5 Detection of the Sniffers
Detecting
the presence of a wireless sniffer, who remains radio-silent, through network
security measures is virtually impossible. Once the attacker begins
probing (i.e., by injecting packets), the presence and the coordinates of the
wireless device can be detected.
4. Wireless Spoofing
There
are well-known attack techniques known as spoofing in both wired and
wireless networks. The attacker constructs frames by filling selected
fields that contain addresses or identifiers with legitimate looking but
non-existent values, or with values that belong to others. The attacker
would have collected these legitimate values through sniffing.
4.1 MAC Address Spoofing
The
attacker generally desires to be hidden. But the probing activity injects
frames that are observable by system administrators. The attacker fills
the Sender MAC Address field of the injected frames with a spoofed value so
that his equipment is not identified.
Typical
APs control access by permitting only those stations with known MAC
addresses. Either the attacker has to compromise a computer system that
has a station, or he spoofs with legitimate MAC addresses in frames that he
manufactures. MAC addresses are assigned at the time of manufacture, but
setting the MAC address of a wireless card or AP to an arbitrary chosen value
is a simple matter of invoking an appropriate software tool that engages in a
dialog with the user and accepts values. Such tools are routinely included
when a station or AP is purchased. The attacker, however, changes the MAC
address programmatically, sends several frames with that address, and repeats
this with another MAC address. In a period of a second, this can happen
several thousand times.
When
an AP is not filtering MAC addresses, there is no need for the attacker to use
legitimate MAC addresses. However, in certain attacks, the attacker
needs to have a large number of MAC addresses than he could collect by
sniffing. Random MAC addresses are generated. However, not every
random sequence of six bytes is a MAC address. The IEEE assigns globally
the first three bytes, and the manufacturer chooses the last three bytes.
The officially assigned numbers are publicly available. The attacker
generates a random MAC address by selecting an IEEE-assigned three bytes
appended with an additional three random bytes.
4.2 IP spoofing
Replacing
the true IP address of the sender (or, in rare cases, the destination)
with a different address is known as IP spoofing. This is a
necessary operation in many attacks.
The
IP layer of the OS simply trusts that the source address, as it appears in an
IP packet is valid. It assumes that the packet it received indeed was
sent by the host officially assigned that source address. Because the IP layer
of the OS normally adds these IP addresses to a data packet, a spoofer must
circumvent the IP layer and talk directly to the raw network device. Note
that the attacker’s machine cannot simply be assigned the IP address of another
host X using
ifconfig or a
similar configuration tool. Other hosts, as well as X, will discover (through
ARP, for example) that there are two machines with the same IP address.
IP
spoofing is an integral part of many attacks. For example, an attacker
can silence a host A from sending further packets to B by sending a spoofed
packet announcing a window size of zero to A as though it originated from B.
4.3 Frame Spoofing
The
attacker will inject frames that are valid by 802.11 specifications, but whose
content is carefully spoofed as described above.
Frames
themselves are not authenticated in 802.11 networks. So when a frame has
a spoofed source address, it cannot be detected unless the address is wholly
bogus. If the frame to be spoofed is a management or control
frame, there is no encryption to deal with. If it is a data frame,
perhaps as part of an on-going MITM attack, the data payload must be properly
encrypted.
Construction
of the byte stream that constitutes a spoofed frame is a programming matter
once the attacker has gathered the needed information through sniffing and
probing. There are software libraries that ease this task.
Examples of such libraries are
libpcap
(sourceforge.net/projects/libpcap/), libnet (libnet.sourceforge.net/), libdnet (libdnet.
sourceforge.net/) and libradiate
(www.packetfactory.net/projects/libradiate/ ).
The
difficulty here is not in the construction of the contents of the frame, but in
getting, it radiated (transmitted) by the station or an AP. This requires
control over the firmware and driver of the wireless card that may sanitize
certain fields of a frame. Therefore, the attacker selects his equipment
carefully. Currently, there are off-the-shelf wireless cards that can be
manipulated. In addition, the construction of special purpose wireless
cards is within the reach of a resourceful attacker.
5. Wireless Network Probing
Even
though the attacker gathers considerable amount of information regarding a
wireless network through sniffing, without revealing his wireless presence at
all, there are pieces that may still be missing. The attacker then sends
artificially constructed packets to a target that trigger useful responses.
This activity is known as probing or active scanning.
The
target may discover that it is being probed, it might even be a honey
pot (www.honeynet.org/)
target carefully constructed to trap the attacker. The attacker would try
to minimize this risk.
5.1 Detection of SSID
Detection
of SSID is often possible by simply sniffing Beacon frames as describe in a
previous section.
If Beacon
transmission is disabled, and the attacker does not wish to patiently wait
for a voluntary Associate Request to appear from a legitimate station that
already has a correct SSID, or Probe Requests from legitimate stations, he will
resort to probing by injecting a Probe Request frame that contains a spoofed
source MAC address. The Probe Response frame from the APs will contain,
in the clear, the SSID and other information similar to that in the Beacon
frames were they enabled. The attacker sniffs these Probe Responses and
extracts the SSIDs.
Some
models of APs have an option to disable responding to Probe Requests that do
not contain the correct SSID. In this case, the attacker determines a station
associated with the AP, and sends the station a forged Disassociation frame
where the source MAC address is set to that of the AP. The station will
send a Reassociation Request that exposes the SSID.
5.2 Detection of APs and stations
Every
AP is a station, so SSIDs, MAC addresses are gathered as described above.
Certain
bits in the frames identify that the frame is from an AP. If we assume
that WEP is either disabled or cracked, the attacker can also gather the IP
addresses of the AP and the stations.
5.3 Detection of Probing
Detection
of probing is possible. The frames that an attacker injects can also be heard
by the intrusion detection systems (IDS) of hardened wireless LAN. There
is GPS-enabled equipment that can identify the physical coordinates of a
wireless device through which the probe frames are being transmitted.
6. AP Weaknesses
APs
have weaknesses that are both due to design mistakes and user interfaces that
promote weak passwords, etc. It has been demonstrated by many publicly
conducted war-driving efforts (www.worldwidewardrive.org) in major cities
around the world that a large majority of the deployed APs are poorly
configured, most with WEP disabled, and configuration defaults, as set up the
manufacturer, untouched.
6.1 Configuration
The
default WEP keys used are often too trivial. Different APs use different
techniques to convert the user’s key board input into a bit vector.
Usually 5 or 13 ASCII printable characters are directly mapped by concatenating
their ASCII 8-bit codes into a 40-bit or 104-bit WEP key. A stronger key
can be constructed from an input of 26 hexadecimal digits. It is possible to
form an even stronger104 bit WEP key by truncating the MD5 hash of an arbitrary
length pass phrase.
6.2 Defeating MAC Filtering
Typical
APs permit access to only those stations with known MAC addresses. This
is easily defeated by the attacker who spoofs his frames with a MAC address
that is registered with the AP from among the ones that he collected through
sniffing. That a MAC address is registered can be detected by observing
the frames from the AP to the stations.
6.3 Rogue AP
Access
points that are installed without proper authorization and verification that
overall security policy is obeyed are called rogue APs. These
are installed and used by valid users. Such APs are configured poorly,
and attackers will find them.
6.4 Trojan AP
An
attacker sets up an AP so that the targeted station receives a stronger signal
from it than what it receives from a legitimate AP. If WEP is enabled,
the attacker would have already cracked it. A legitimate user selects the
Trojan AP because of the stronger signal, authenticates and associates.
The Trojan AP is connected to a system that collects the IP traffic for later
analyses. It then transmits all the frames to a legitimate AP so that the
victim user does not recognize the on-going MITM attack. The attacker can steal
the users password, network access, compromise the user’s system to give
himself root access. This attack is called the Evil Twin Attack.
It
is easy to build a Trojan AP because an AP is a computer system optimized for
its intended application. A general purpose PC with a wireless card can
be turned into a capable AP. An example of such software is HostAP (http://hostap.epitest.fi/
). Such a Trojaned AP would be formidable.
6.5 Equipment Flaws
A
search on www.securityfocus.com
with “access point vulnerabilities” will show that numerous flaws in equipment
from well-known manufacturers are known. For example, one such AP crashes
when a frame is sent to it that has the spoofed source MAC address of
itself. Another AP features an embedded TFTP (Trivial File Transfer
Protocol) server. By requesting a file named
config.img
via TFTP, an attacker
receives the binary image of the AP configuration. The
image includes the administrator’s password required by the HTTP user
interface, the WEP encryption keys, MAC address, and SSID. Yet another AP
returns the WEP keys, MAC filter list, administrator’s password when sent a UDP
packet to port 27155 containing the string “
gstsearch”.
It
is not clear how these flaws were discovered. The following is a likely
procedure. Most manufacturers design their equipment so that its firmware
can be flashed with a new and improved one in the field. The firmware
images are downloaded from the manufacturers’ web site. The CPU used in
the APs can be easily recognized, and the firmware can be systematically disassembled
revealing the flaws at the assembly language level.
Comprehensive
lists of such equipment flaws are likely circulating among the attackers.
7. Denial of Service
A
denial of service (DoS) occurs when a system is not providing services
to authorized clients because of resource exhaustion by unauthorized
clients. In wireless networks, DoS attacks are difficult to prevent,
difficult to stop an on-going attack and the victim and its clients may not
even detect the attacks. The duration of such DoS may range from milliseconds
to hours. A DoS attack against an individual station enables session
hijacking.
7.1 Jamming the Air Waves
A
number of consumer appliances such as microwave ovens, baby monitors, and
cordless phones operate on the unregulated 2.4GHz radio frequency. An attacker
can unleash large amounts of noise using these devices and jam the airwaves so
that the signal to noise drops so low, that the wireless LAN ceases to
function. The only solution to this is RF proofing the surrounding environment.
7.2 Flooding with Associations
The
AP inserts the data supplied by the station in the Association Request into a
table called the association table that the AP maintains in its
memory. The IEEE 802.11 specifies a maximum value of 2007 concurrent
associations to an AP. The actual size of this table varies among
different models of APs. When this table overflows, the AP would refuse
further clients.
Having
cracked WEP, an attacker authenticates several non-existing stations
using legitimate-looking but randomly generated MAC addresses. The
attacker then sends a flood of spoofed associate requests so that the
association table overflows.
Enabling
MAC filtering in the AP will prevent this attack.
7.3 Forged Dissociation
The
attacker sends a spoofed Disassociation frame where the source MAC address is
set to that of the AP. The station is still authenticated but needs only to
reassociate and sends Reassociation Requests to the AP. The AP may send a
Reassociation Response accepting the station and the station can then resume
sending data. To prevent Reassociation, the attacker continues to send
Disassociation frames for a desired period.
7.4 Forged Deauthentication
The
attacker monitors all raw frames collecting the source and destination MAC
addresses to verify that they are among the targeted victims. When a data
or Association Response frame is observed, the attacker sends a spoofed
Deauthentication frame where the source MAC address is spoofed to that of the
AP. The station is now unassociated and unauthenticated, and needs to
reconnect. To prevent a reconnection, the attacker continues to send
Deauthentication frames for a desired period. The attacker may even rate
limit the Deauthentication frames to avoid overloading an already congested
network.
The
mischievous packets of Disassociation and Deauthentication are sent
directly to the client, so these will not be logged by the AP or IDS, and
neither MAC filtering nor WEP protection will prevent it.
7.5 Power Saving
Power
conservation is important for typical station laptops, so they frequently enter
an 802.11 state called Doze. An attacker can steal packets intended for
a station while the station is in the Doze state.
The
802.11 protocol requires a station to inform the AP through a successful frame
exchange that it wishes to enter the Doze state from the Active state.
Periodically
the station awakens and sends a PS-Poll frame to the AP. The AP will transmit
in response the packets that were buffered for the station while it was dozing.
This polling frame can be spoofed by an attacker causing the AP to
send the collected packets and flush its internal buffers. An attacker can
repeat these polling messages so that when the legitimate station periodically
awakens and polls, AP will inform that there are no pending packets.
8. Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attack
refers to the situation where an attacker on host X inserts X between all
communications between hosts B and C, and neither B nor C is aware of the
presence of X. All messages sent by B do reach C but via X, and vice
versa. The attacker can merely observe the communication or modify it
before sending it out. An MITM attack can break connections that are
otherwise secure. At the TCP level, SSH and VPN, e.g., are prone to this
attack.
8.1 Wireless MITM
Assume
that station B was authenticated with C, a legitimate AP. Attacker X is a
laptop with two wireless cards. Through one card, he will present X as an
AP. Attacker X sends Deauthentication frames to B using the C’s MAC
address as the source, and the BSSID he has collected. B gets
deauthenticated and begins a scan for an AP and may find X on a channel
different from C. There is a race condition between X and C. If B
associates with X, the MITM attack succeeded. X will re-transmit the
frames it receives from B to C, and the frames it receives from C to B after
suitable modifications.
The
package of tools called AirJack (http://802.11ninja.net/airjack/) includes a
program called
monkey_jack
that automates the MITM attack. This is programmed well so that the odds
of it winning in the race condition mentioned above are improved.8.2 ARP Poisoning
ARP
cache poisoning is an old problem in wired networks. Wired networks have
deployed mitigating techniques. But, the ARP poisoning technique is
re-enabled in the presence of APs that are connected to a switch/hub along with
other wired clients.
ARP
is used to determine the MAC address of a device whose IP address is known. The
translation is performed with a table look-up. The ARP cache
accumulates as the host continues to network. If the ARP cache does not
have an entry for an IP address, the outgoing IP packet is queued, and an ARP
Request packet that effectively requests “If your IP address matches this
target IP address, then please let me know what your Ethernet address is” is
broadcast. The host with the target IP is expected to respond with an ARP
Reply, which contains the MAC address of the host. Once the table is
updated because of receiving this response, all the queued IP packets can now
be sent. The entries in the table expire after a set time in order to account
for possible hardware address changes for the same IP address. This change may
have happened, e.g., due to the NIC being replaced.
Unfortunately,
the ARP does not provide for any verification that the responses are from valid
hosts or that it is receiving a spurious response as if it has sent an ARP
Request. ARP poisoning is an attack technique exploiting this lack of
verification. It corrupts the ARP cache that the OS maintains with wrong
MAC addresses for some IP addresses. An attacker accomplishes this by sending
an ARP Reply packet that is deliberately constructed with a “wrong” MAC
address. The ARP is a stateless protocol. Thus, a machine receiving
an ARP Reply cannot determine if the response is due to a request it sent or
not.
ARP
poisoning is one of the techniques that enables the man-in-the-middle attack.
An attacker on machine X inserts himself between two hosts B and C by (i)
poisoning B so that C’s IP address is associated with X’s MAC address, (ii)
poisoning C so that B’s address is associated with X’s MAC address, and (iii) relaying
the packets X receives.
The
ARP poison attack is applicable to all hosts in a subnet. Most APs act as
transparent MAC layer bridges, and so all stations associated with it are
vulnerable. If an access point is connected directly to a hub or a switch
without an intervening router/firewall, then all hosts connected to that hub or
switch are susceptible also. Note that recent devices aimed at the home
consumer market combine a network switch with may be four or five ports, an AP,
a router and a DSL/cable modem connecting to the Internet at large.
Internally, the AP is connected to the switch. As a result, an attacker
on a wireless station can become a MITM between two wired hosts, one wired one
wireless, or both wireless hosts.
The
tool called Ettercap ((http://ettercap.sourceforge.net) is capable
of performing ARP poisoning.
8.3 Session Hijacking
Session
hijacking occurs in the context of a “user”, whether human or
computer. The user has an on-going connection with a server.
Hijacking is said to occur when an attacker causes the user to lose his
connection, and the attacker assumes his identity and privileges for a period.
An
attacker disables temporarily the user’s system, say by a DoS attack or a
buffer overflow exploit. The attacker then takes the identity of the
user. The attacker now has all the access that the user has. When
he is done, he stops the DoS attack, and lets the user resume. The user
may not detect the interruption if the disruption lasts no more than a couple
of seconds. Such hijacking can be achieved by using forged
Disassociation DoS attack.
Corporate
wireless networks are often set up so that the user is directed to an
authentication server when his station attempts a connection with an AP.
After the authentication, the attacker employs the session hijacking described
above using spoofed MAC addresses.
9. War Driving
Equipped
with wireless devices and related tools, and driving around in a vehicle or
parking at interesting places with a goal of discovering easy-to-get-into
wireless networks is known as war driving. War-drivers (http://www.wardrive.net/)
define war driving as “The benign act of locating and logging wireless access
points while in motion.” This benign act is of course useful to the
attackers.
9.1 War chalking
War
chalking is the practice of marking sidewalks and walls with special symbols to
indicate that wireless access is nearby so that others do not need to go
through the trouble of the same discovery. A search on www.google.com
with key words “war driving maps” will produce a large number of hits.
Yahoo! Maps can show "Wi-fi Hotspots" near an address you give.
9.2 Typical Equipment
The
typical war driving equipment consists of a laptop computer system or a PDA
with a wireless card, a GPS, and a high-gain antenna. Typical
choice of an operating system is Linux or FreeBSD where open source sniffers
(e.g., Kismet) and WEP crackers (e.g., AirSnort) are available. Similar
tools (e.g., NetStumbler) that run on Windows are available.
War
drivers need to be within the range of an AP or station located on the target
network. The range depends on the transmit output power of the AP
and the card, and the gain of the antenna. Ordinary access point antennae
transmit their signals in all directions. Often, these signals reach
beyond the physical boundaries of the intended work area, perhaps to adjacent
buildings, floors, and parking lots. With the typical 30mW wireless cards
intended for laptops, the range is about 300 feet, but there are in 2004
wireless cards for laptops on the market that have 200mW. Directional high-gain
antennae and an RF-amplifier can dramatically extend the range.
10. Wireless Security Best Practices
This
section describes best practices in mitigating the problems described above.
10.1 Location of the APs
APs
should be topologically located outside the perimeter firewalls. The
wireless network segments should be treated with the same suspicion as that for
the public Internet. Additionally, it is important to use directional
antennae and physically locate them in such a way that the radio-coverage
volume is within the control of the corporation or home.
10.2 Proper Configuration
Statistics
collected by www.worldwidewardrive.org show a distressingly
large percentage of APs left configured with the defaults.
Before
a wireless device is connected to the rest of the existing network, proper
configuration of the wireless device is necessary. The APs come with a
default SSID, such as “Default SSID”, “WLAN”, “Wireless”, “Compaq”, “intel”,
and “linksys”. The default passwords for the administrator accounts that
configure the AP via a web browser or SNMP are well known for all
manufacturers. A proper configuration should change these to difficult to
predict values.
Note
that the SSID serves as a simple handle, not as a password, for a wireless
network. Unless the default SSID on the AP and stations is changed, SSID
broadcasts are disabled, MAC address filtering is enabled, WEP enabled, an
attacker can use the wireless LAN resources without even sniffing.
The
configuration via web browsing (HTTP) is provided by a simplistic web server
built into an AP. Often this configuration interface is provided via both
wired connections and wireless connections. The web server embedded in a
typical AP does not contain secure HTTP, so the password that the administrator
submits to the AP can be sniffed. Web based configuration via wireless
connections should be disabled.
WEP
is disabled in some organization because the throughput is then higher.
Enabling WEP encryption makes it necessary for the attacker intending to
WEP-crack to have to sniff a large number of frames. The higher the
number of bits in the encryption the larger the number of frames that must be
collected is. The physical presence in the radio range of the equipment for
long periods increases the odds of his equipment being detected. WEP
should be enabled.
The
IEEE 802.11 does not describe an automated way of distributing the
shared-secret keys. In large installations, the manual distribution of
keys every time they are changed is expensive. Nevertheless, the WEP encryption
keys should be changed periodically.
10.3 Secure Protocols
If
the WEP is disabled, or after the WEP is cracked, the attacker can capture all
TCP/IP packets by radio-silent sniffing for later analyses. All the wired
network attacks are possible. There are real-time tools that analyze and
interpret the TCP/IP data as they arrive.
All
protocols that send passwords and data in the clear must be avoided. This
includes the rlogin family, telnet, and POP3. Instead one should use SSH
and VPN.
In
general, when a wireless segment is involved, one should use end-to-end
encryption at the application level in addition to enabling WEP.
10.4 Wireless IDS
A
wireless intrusion detection system (WIDS) is often a self-contained computer
system with specialized hardware and software to detect anomalous
behavior. The underlying software techniques are the same hacking
techniques described above. The special wireless hardware is more capable
than the commodity wireless card, including the RF monitor mode, detection of
interference, and keeping track of signal-to-noise ratios. It also
includes GPS equipment so that rogue clients and APs can be located. A
WIDS includes one or more listening devices that collect MAC addresses, SSIDs,
features enabled on the stations, transmit speeds, current channel, encryption
status, beacon interval, etc. Its computing engine will be powerful enough
that it can dissect frames and WEP-decrypt into IP and TCP components.
These can be fed into TCP/IP related intrusion detection systems.
Unknown
MAC addresses are detected by maintaining a registry of MAC addresses of known
stations and APs. Frequently, a WIDS can detect spoofed known MAC
addresses because the attacker could not control the firmware of the wireless
card to insert the appropriate sequence numbers into the frame.
10.5 Wireless Auditing
Periodically,
every wireless network should be audited. Several audit firms provide
this service for a fee. A security audit begins with a well-established
security policy. A policy for wireless networks should include a
description of the geographical volume of coverage. The main goal of an
audit is to verify that there are no violations of the policy. To this
end, the typical auditor employs the tools and techniques of an attacker.
10.6 Newer Standards and Protocols
Many
improvements in wireless network technology are proposed through proprietary
channels (e.g., Cisco Lightweight Extensible Authentication Protocol) as well
as through the IEEE. The new IEEE 802.11i (ratified in June 2004)
enhances the current 802.11 standard to provide improvements in security.
These include Port Based Access Control for authentication, Temporal Key
Integrity Protocol for dynamic changing of encryption keys, and Wireless Robust
Authentication protocol. An interim solution proposed by vendors is the
Wi-Fi Protected Access (WPA), a subset of 802.11i, is only now becoming
available in some products. Time will tell if these can withstand future
attacks.
10.7 Software Tools
Below
we describe a collection of cost-free tools that can be used both as attack
tools and as audit tools.
· AirJack
(http://802.11ninja.net/airjack/)
is a collection of wireless card drivers and related programs. It
includes a program called
monkey_jack
that automates the MITM attack. Wlan_jack
is a DoS tool that accepts a target source and BSSID to send continuous
deauthenticate frames to a single client or an entire network (broadcast
address). Essid_jack sends a
disassociate frame to a target client in order to force the client to
reassociate with the network, thereby giving up the network SSID.
11. Conclusion
This
article is an introduction to the techniques an attacker would use on wireless
networks. Regardless of the protocols, wireless networks will remain
potentially insecure because an attacker can listen in without gaining physical
access. In addition, the protocol designs were security-naïve. We
have pointed out several existing tools that implement attack techniques that
exploit the weaknesses in the protocol designs. The integration of
wireless networks into existing networks also has been carelessly done.
We pointed out several best practices that can mitigate the insecurities.
GLOSSARY
AP: Access Point. Any entity that has station
functionality and provides access to the distribution services, via the
wireless medium for associated stations.
Association
Table: The Association table is within an AP and controls the routing of all
packets between the Access Point and the wireless devices in a WLAN.
Basic Service Set: BSS is a collection, or set, of
stations that are logically associated with each other and controlled by a
single AP. Together, they operate as a fully connected wireless network.
Basic Service Set Identifier (BSSID): A 48-bit identifier
used by all stations in a Basic Service Set as part of the frame header.
Beacon: A wireless LAN frame broadcast by access
points that signals their availability.
Evil Twin Attack. An unauthorized AP whose goal is to
masquerade as an existing legitimate/ authorized AP is called an Evil
Twin. The evil twin AP is designed and located so that client stations
receive stronger signals from it. Legitimate users are lured into the
evil twin, and unknowingly give away user IDs and passwords.
Independent BSS: An IBSS is usually an ad-hoc network. In
an IBSS, all of the stations are responsible for sending beacons.
IDS: Intrusion detection system.
MITM: Man in the middle. See Section 8.
Service
Set Identifier (SSID): All APs and stations within the same wireless network
use an identifier that is up to 32-bytes long.
Social
Engineering: Social engineering is a term, coined in jest that refers to all
non-technical methods of collecting information about a person so that the
passwords the person may use can be predicted. The methods of collection
range from dumpster diving, analyzing the publicly available information to
making phone calls impersonating others.
STA:
A wireless station.
WEP:
Wired Equivalent Privacy (WEP) is a shared-secret key encryption system used to
encrypt packets transmitted between a station and an AP.
|



